USITCC Regionals Security Preperation

Hey! This article is a written version of the topics that I went over in my recent talk to the Association of Business Information Technology students about cybersecurity a full link to the presentation as well as video is below this paragraph:
(This will be updated with the video once taken)
Sections of the Competition
How the Regional / National USITCC competition is setup
Written Section
50 - 70 multiple choice test, similar to CompTIA Security+ and other security certifications This mostly covers questions that you can have multiple choice questions on. I would recommend looking at the Security+ exam objectives
Capture the flag
The top 10% from the written test move on to a CTF starting as soon as the last person is done taking the written exam. This covers practical application and is the majority of the topics covered. Nationals consisted mostly of log analysis and forensics. It is to be seen if they will add additional areas based on ethical hacking.
Topics covered:
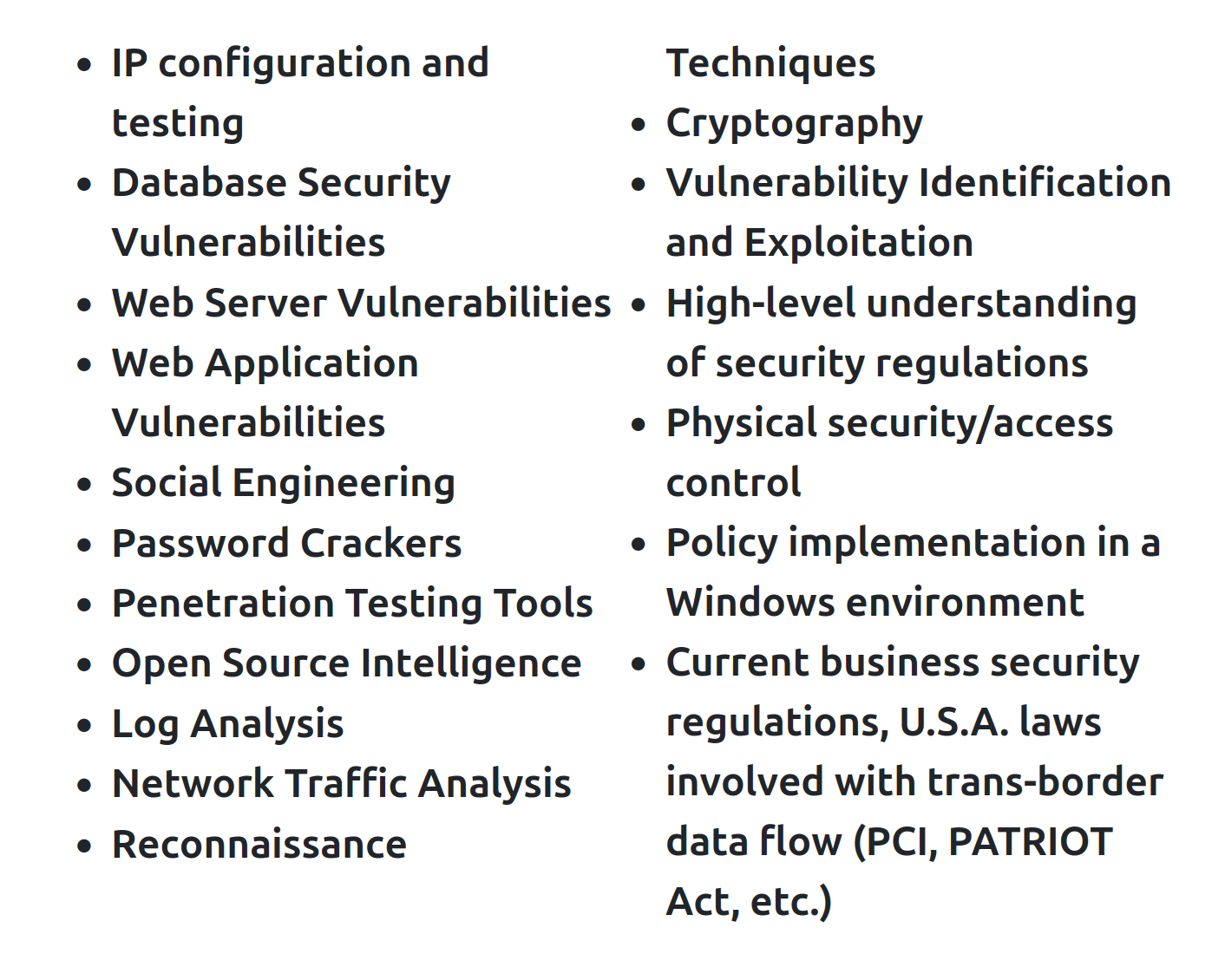
Resources
Item's I've collected to help you study for the USITCC Security Competition
Hack the box / Try hack me
Hack the box provides great resources to complete "Boxes" in order to practice what CTF challenges will look like
Hack the box hosts CTF's too take a look at a couple here to get your feet wet into cyber
October 24th - 26th

Hack the box CTF occuring this weekend.

University CTF
News Sites
I use an RSS feed on my phone to get the latest in news from several different cybersecurity websites I highly recomend taking some time to look at large new articles and events in cyber!
My current list:
- 0day Fans
- Bleeping Computer
- Cyber Security News
- The Register - Security
- Dark Reading
MITRE Vectors
Want to know how malware works? check out the Mitre ATT&CK to find out about malware tactics for many different things

Mitre ATT&CK Vectors list
CompTIA Security+ Exam Objectives (Written study guide basically)
Networking
A quick jump into computer networking
IP Addressing
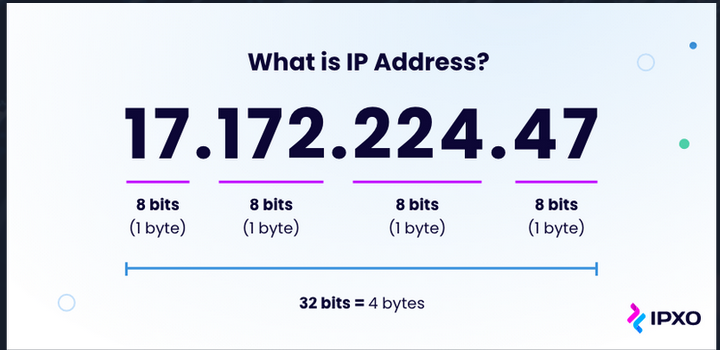
What is an IP Address? Its basically the phone number of the internet. You use the 32 bits in a ip address to reach a different machine. These addresses are assigned by the router to a machine to allow other computers to contact it. The router then does Network Address Translation (NAT) to translate that IP address into a MAC address to ensure its delivered to the correct location.
CIDR Notation
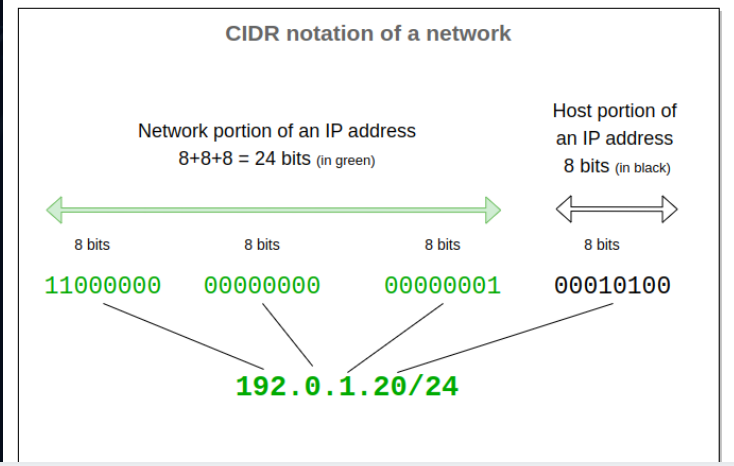
The CIDR notation describes how IP addresses are assigned in a network. The /24 notation shows that the first 24 bits (8+8+8) will be assigned to be the "Network" and will not change on any of the ip addresses assigned while the "host" bits are the last 8 and will change based on the machine.
Web security
Talking about vulnerabilities affecting websites.
Broken Access Control
Users can act outside of their intended permissions from viewing folders they shouldn’t be able to. to finding files not intended for public display
Here a fun google dork as a demonstration:
“not for public release filtype:pdf”

Google search fill in for a not for public release files
Cryptographic Failures
Lack of encryption, passwords or data stored in plaintext. card data not encrypted etc.
Meta was recently fined $102 million dollars for storing Facebook passwords in plain text. This was a cryptographic failure from Meta. I'm sure they've had a great time "investigating" why they haven't hashed their passwords for four years.

Injection
User input is dangerous and without the proper safeguards can cause a system to do something it normally shouldn't as an example you can use a sql injection:
“ or “”=” in the password field if not properly sanitized to log right in to an account
Juice shop
For demonstration in the presentation we take a look at the OWASP juice shop. a web hackable application that is super easy to host. demonstrating some simple attacks against the machine.
Cryptography
01000011 01110010 01111001 01110000 01110100 01101111 01100111 01110010 01100001 01110000 01101000 0111100101000011 01110010 01111001 01110000 01110100 01101111 01100111 01110010 01100001 01110000 01101000 01111001
“Cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. The art of cryptography has been used to code messages for thousands of years and continues to be used in bank cards, computer passwords, and ecommerce.” -Fortinet
- Traces its roots back to Julius Caesar (Caesar Cipher)
- 1970s IBM developed Data Encryption Standard (DES) Algorithm
- 1977 RSA Algoritm was published
Types
- Symmetric Key Encryption
- One key to encrypt / decrypt
- A-Symmetric Key
- Public / Private key pairs
Algorithms
Rivest - Shadmir - Aldeman (RSA)
Public-Key System Developed for Intelligence encroyption
Uses two large prime numbers
Factoring two prime numbers is near impossible

Data Encryption Standard (DES)
First main computer encryption standard Replaced by triple DES With three keys of 56 bytes
Phased out and has been broken many times

Advanced Encryption Standard (AES)
This is the current government standard using keys of 192 and 256 bits
_Round_Function.png)
Quantum Computers
Each year the amount of bits of a key that quantum can hack grows, the latest one was 22-bit keys. This has put NIST in a rush to get new standards for encryption out and ready to go for when not if quantum computers are able to crack our encryption.
The swiss army knife for all things encryption
Regulations
Types of Controls
Management
Security controls that focus on the management of risk and management of information system security.
Operational
Implemented to be executed by people This would be procedural. How data is handled, where its stored and the policies an organziation operates by
Technical
The controls implemented that are executed by the computer. Not people. I/e Multi Factor Authentication, Password Policies, etc
Control Types
Preventative
Work to prevent an incident from occurring
Examples: Firewalls encryption system hardening malware detection
Detective
Detect incidents after they have occurred
Examples: Audit logs, Intrusion Detection Systems, Security Information and Event Management (SIEM Systems), Vulnerability Scanning
Corrective
Last line of defense against cyber threats, They correct the impact of an incident
Data recovery, incident response, data backups
Deterrent
Attempt to discourage individuals into causing incidents
Compensating
When primary controls are unfeasible or require enhancement and alternative methods are needed to fulfill unmet requirements
Red teaming, Honey pots
Physical
Controls implemented at the physical level to deter or prevent attacks on a system. such as locking down a computer's USB ports
PCI - DSS
Payment Card Industry standards. If you are accepting payments I better hope you are following PCI. Provides core protection through encryption and secure software

Patriot Act
War on terror act. Affecting information disclosures by organizations in national security incidents. Requring disclosure from ISP’s
Signed by George W Bush in October 26 2001
GDPR
You seen those cookie pop ups? Thank GDPR
Applies to people in the European Union protecting their data from being stored outside of the EU. Millions of dollars of fines come every month out of this regulation

Recent Events
Crowdstrike
Largest IT Outage in HISTORY. $5 billion dollars worth of direct losses according to one insurer July 2024.
8 million computers blue screened constantly due to an error in the root driver caused by a channel file being added with 12 parameters instead of 13.
Russian Attacks
Advent of the Russia / Ukraine war has seen a massive increase in cyber attacks and shown us how cyber attacks have become weapons of war
February 2022 Many russian officers in unit 29155 were indicted for large-scale cyber attacks against ukraine.
September 4th the U.S Filed charges against employees of the Russian media group network RT in an effort to hire a company to influence the 2024 election using shell companies and personas
Blackouts in ukraine caused by malware “Industroyer One and Two”
Pollyfill.io
Attacked the pollyfill library used by websites researchers at sensec discovered java script code injected into 110,000 websites including phishing and advertising on June 25th (They even got ddosed on the 26th)
Code was based on http headers, one redirected mobile users to a sports betting site using the domain ww.googie-anaiytics.com only activating at specific hours or against admin users or web analytics.
https://sansec.io/research/polyfill-supply-chain-attack
if the internet archive works:
http://web.archive.org/web/20240000000000*/pollyfill.io
https://www.csis.org/programs/strategic-technologies-program/significant-cyber-incidents
Conclusion
Thanks for sticking it out!
I wish you luck in the security competition this year! Kind of weird how I'm training my competitors. But I think everyone deserves a slice of this cyber knowledge! if you have any questions you can reach out to me at my missouri state email or olsontyler@proton.me
Can't wait for day 2! After working on this I'll be setting up the infrastructure for our practice capture the flag!





